Learn how to use Facebook for OSINT investigations. Explore practical techniques, tools, and data points, from profile analysis to reverse image searches, to uncover actionable intelligence safely and effectively.
Social media is a gold mine for open-source intelligence (OSINT). Among all platforms, Facebook OSINT stands out for its depth and diversity, enabling investigators to extract valuable clues about individuals, organizations, and digital footprints using OSINT tools for Facebook.
In this Facebook OSINT guide, we’ll show how investigators can safely collect and analyze intelligence from Facebook profiles, pages, and groups. You’ll learn practical techniques, tools, and workflows to extract actionable information—all while remaining secure and anonymous.
This article builds on our broader social media intelligence (SOCMINT) series covering OSINT methods for platforms like Mastodon, Reddit, X, Instagram, and Discord. Before diving into investigation techniques, we’ll briefly cover Facebook’s structure and why it remains one of the most valuable sources for digital intelligence gathering.
Here is a quick overview of the steps we’ll cover for how to use Facebook in OSINT research:
- Inspecting Facebook profiles: How to extract user information, connections, and behavioral insights safely
- Retrieving identifiers: Techniques for finding Facebook user IDs, usernames, and display names for cross-platform searches
- Analyzing multimedia content: How to assess profile and cover photos, videos, and metadata for investigative value
- Using reverse image and sentiment analysis tools: Ways to uncover linked accounts and emotional cues from posts
- Investigating contact and bio details: Methods for analyzing emails, phone numbers, and linked websites in Facebook bios
- Examining posts and engagement: Interpreting reactions, comments, and shares to reveal social patterns and affiliations
- Applying secure research practices: How to conduct Facebook OSINT investigations safely with platforms like Silo
Quick tip: To perform Facebook OSINT safely, always use secure research environments such as Silo. These platforms isolate your browsing activity, protect your identity, and ensure compliance with organizational or legal policies during open-source intelligence Facebook investigations.
Why Facebook matters for OSINT
Facebook, now under Meta Platforms, Inc., was launched in 2004 by Mark Zuckerberg and his college roommates. The platform is considered the largest social media platform globally, with more than 3.07 billion monthly active users worldwide as of September 2024 (see Figure 1). The large user base and the diverse global societies that use Facebook services have made it a crucial source for gathering intelligence across various fields, including law enforcement, military, intelligence, marketing, and academic research.
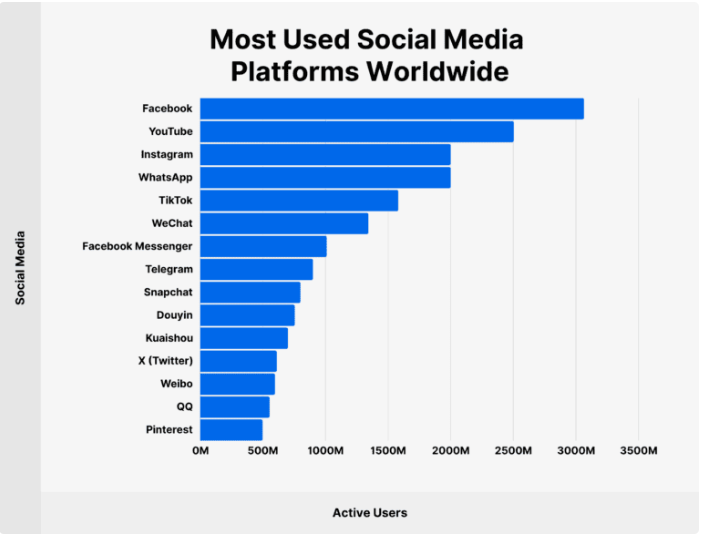
Figure 1 - Most used social media platform worldwide, Facebook is still the first one. Source: https://backlinko.com/facebook-users
Facebook's diverse features, such as users' personal profiles, business pages, groups, and events, appeal to OSINT investigators and provide multiple avenues for them to collect valuable information. Facebook’s users range in age, belonging to both the older generations and Generation Z, unlike some platforms like TikTok, where most of the users are younger.
Searching within Facebook is challenging for OSINT researchers due to the complex privacy settings and frequent policy and search changes by Meta. This underscores the urgency and importance of staying updated on the latest OSINT techniques specific to Facebook, as it is crucial for effective data collection.
The foundation of Facebook's social media network is composed of the following four features:
- Profiles
- Pages
- Groups
- Events
The focus of this guide will be to discuss how to inspect individuals’ profiles on Facebook.
How to analyze Facebook profiles for OSINT
Inspecting Facebook profiles for OSINT reveals essential information about a target’s identity, social circle, and behavior. Using Facebook investigation techniques, analysts can map networks, detect patterns, and cross-reference data across multiple platforms.
Here are the key OSINT data points in a typical Facebook profile:
- Basic info: name, location, birthday
- Work and education details
- Friends and family connections
- Liked pages and groups
- Check-ins and locations
These insights reveal user networks, interests, and behaviors for OSINT research. Let’s dig into each one.
Basic information
Basic information includes Facebook username, personal name, gender, birthday, hometown, and geographic location. Seeing this information depends on the user's current privacy settings. However, it is common for Facebook users to display such information publicly, making it easy to track their demographic and geographical background (see Figure 2).
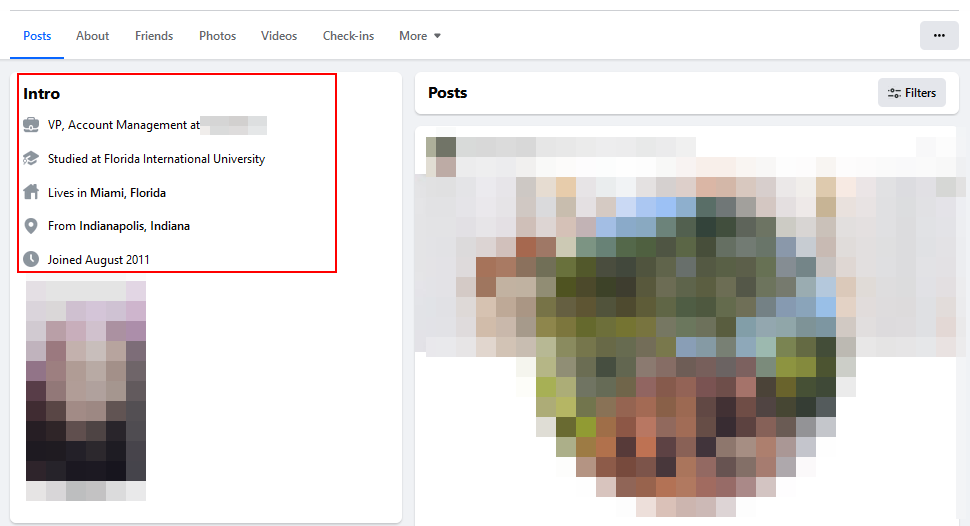
Figure 2 - The Intro section of the Facebook profile may show important information about the user, such as account creation date, hometown, current location and employer
Employment and education
Employment and education includes job titles; companies worked for, past and present; and schools attended. Most users share such information, which helps OSINT reveal work history and educational background.
Relationship insights
Relationship insights include a friends list and family details. If a user privacy setting allows showing a friends list, then it can reveal social connections and networks, which helps map relationships or identify associates (see Figure 3).
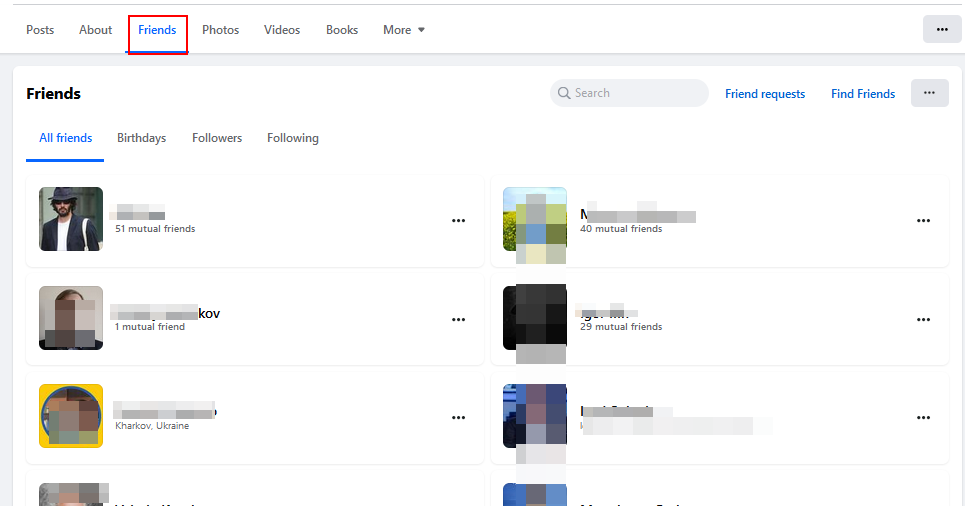
Figure 3 - Checking the list of Friends of a Facebook user
Family details
Some users list family members and marital status, providing clues about their personal relationships and extended networks. If this information is not shared directly, checking posted photos, videos, and tags can reveal such relationships.
Behavior and interests
Behavior and interests include post and status updates, liked pages and groups, check-ins, and locations.
Posts and status updates
Facebook users often post about their daily lives, political views, hobbies, and interests. This gives insight into target users' behavior, daily routines, and thinking. We can also check the other pages in the target profile, such as Sports, Music, Movies, TV shows, Books, Apps and Games, Likes, Events, and Reviews given (see Figure 4).
All these pages reveal much information about the target profile's personality and interests. For example, analyzing target user preferences in music, books, and movies can reveal their cultural tastes, political views, or religious beliefs.
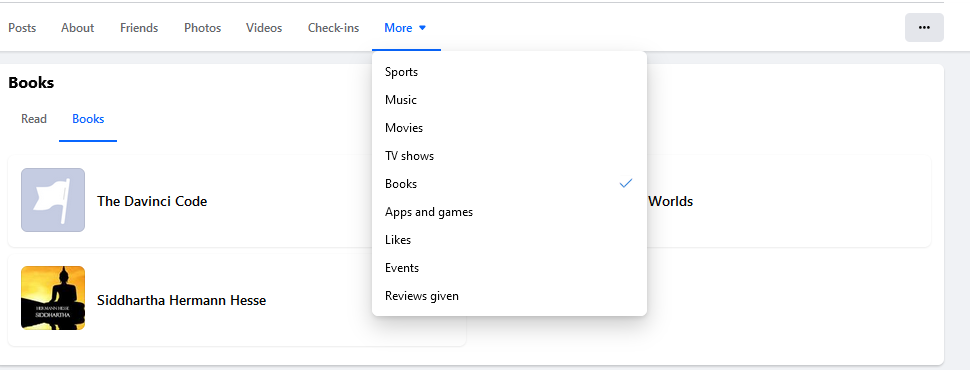
Figure 4 - Check the top links in the target Facebook profile page to access more information about user interests and hobbies
Liked pages and groups
Pages and groups followed by a Facebook user can reveal ideological thinking, brand affiliations or memberships in specific communities (e.g., local social groups, professional societies, etc.).
Check-ins and locations
Location-tagged posts or check-ins can map a person's geographical movements, such as revealing travel habits or frequented places (see Figure 5).
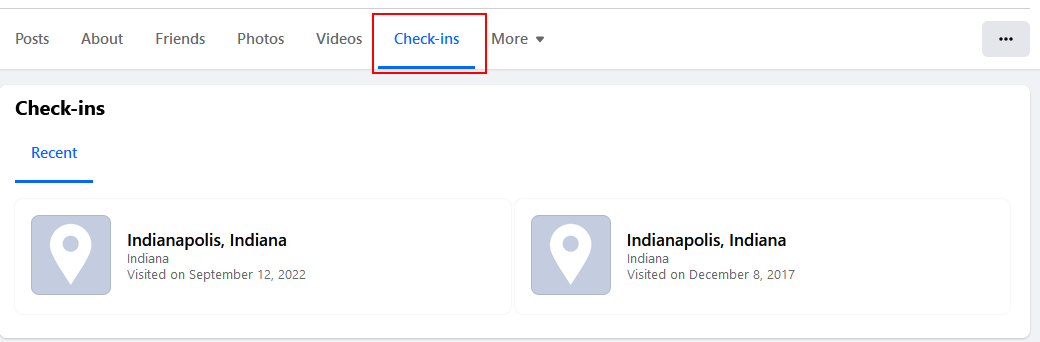
Figure 5 - Check-ins reveal important information about the target user's previous locations and the date when they visited them
Analyzing multimedia content
Multimedia content includes photos and videos. Photos can be images shared publicly, showing details about a user's physical appearance, possessions (watches, cars, house), locations visited, or social circles (friends and family). OSINT researchers can also exploit metadata (such as timestamps and geotags) embedded in media files for more info.
Visual analysis
The first thing we need to do is visually analyze profile pictures. They may reveal information about the user's personal preferences, interests, hobbies, lifestyle or current location by checking any landmarks or geographical features in the photos. Some users may make their Facebook profile locked. Hence, we cannot click the profile image or cover photo to display the large size. In that case, we can use enlargement services to enlarge the picture and make its details clearer. Here are some free online image enlargement services:
Images and video metadata
Digital files, such as photos and videos, contain metadata. Metadata is data about data and it provides important information about the file. For example, image metadata may contain the GPS coordinates showing where the image was captured, the capturing device type (smartphone or camera model), the date and time when the photo was captured and other technical information like shutter speed and ISO settings.
Unfortunately, Facebook removes EXIF metadata from uploaded media content for privacy reasons. This practice helps protect users' sensitive information buried within digital media files, such as geographical location data, from being unintentionally revealed. However, you may prefer to inspect images and videos found on Facebook for any remaining metadata. In that case, you can use the following tools (please note that these tools can only reveal metadata that Facebook has not stripped away):
- ExifTool by Phil Harvey
- EXIF.tools – an online tool
- Exif Pilot
- Gimphoto
Reverse image search
Facebook profiles and cover images should be reverse-searched to see where they appear online. We should also reverse search any image on the target Facebook feed or included in their comments. Here are some search engines for conducting reverse image searches:
If you prefer using an extension for reverse image search, you can use the "Search by Image" Chrome extension. It allows you to conduct a reverse image search across different platforms.
Emotional analysis
For personal photos, we can conduct an emotional analysis to determine the user's emotional status when they took the picture. Here are some tools for executing emotional analysis on a picture containing a human face.
- FaceReader: A professional software for automatic facial expression recognition and analysis (see Figure 6)
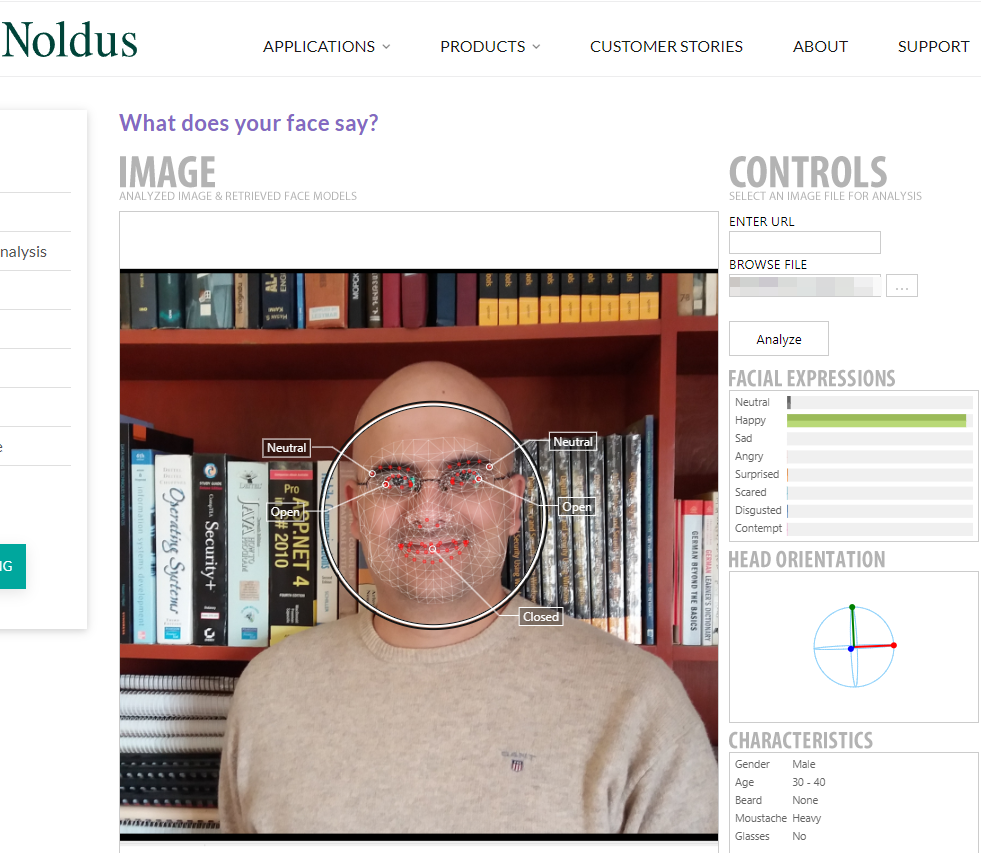
Figure 6 - Using the FaceReader to detect human emotion status from their facial images
- Morphcast: Require email registration to receive a license key
Retrieving user identifiers (IDs, usernames, and display names)
Before beginning to show how to use OSINT techniques to inspect Facebook profiles, let us first explain how to retrieve any Facebook user ID.
Facebook ID
Facebook sets a unique ID for each user profile, page, or group. This ID is a unique numerical identifier assigned to each Facebook account. It is used to track and identify individual users within the Facebook platform.
Here’s how to find a Facebook ID:
- Copy the Facebook profile, page, or group URL.
- Paste it into an ID lookup tool such as Lookup-ID.com or Bulk Facebook ID Finder.
- Copy the unique numerical Facebook ID returned.
Use this ID in other Facebook OSINT tools for profile cross-checking and data correlation.
Facebook username and display name
Each Facebook profile should have a username and a display name. The username is unique and is used to distinguish a user across the Facebook platform. The username is also known as the Facebook handle.
After accessing the target Facebook profile page, the username is found in the page URL. Username is case-insensitive; hence, username is similar to userName. For example, https://www.facebook.com/thunder.weaver.5 The last part of the URL ("thunder.weaver.5") is the username part.
Display names can be anything the user chooses; they commonly point to the Facebook user's actual name. The display name is the one shown on user posts and comments and it is next to the profile photo (see Figure 7).
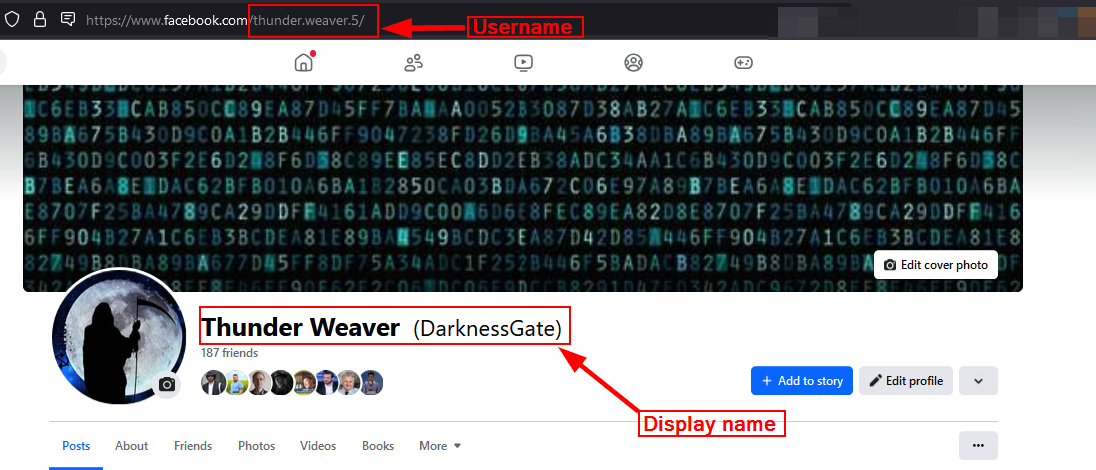
Figure 7 - Facebook username and display name
Many social media users choose to use the same username and display name on different platforms, such as Facebook, X, Reddit, and Mastodon.
There are online services that reverse-search usernames, allowing OSINT gatherers to find all other social media websites where the same username is used.
We can also search for a target Facebook Display Name to see where it appears online using Google dorks. Here are five search queries:
- "Display name" | This query will search for the exact phrase or display name
- "Display Name" site:facebook.com OR site:x.com OR site:instagram.com | Search for display name on three social media platforms
- "Display Name" filetype:pdf OR filetype:doc OR filetype:docx | Search for display name within documents (PDF, DOC, DOCX)
- "Display Name" site:reddit.com OR site:quora.com OR site:forums.example.com | This query searches for display name on popular discussion forums
- "Display Name" blog OR article | This query searches for blog posts and articles that mention the specified display name (see Figure 8)
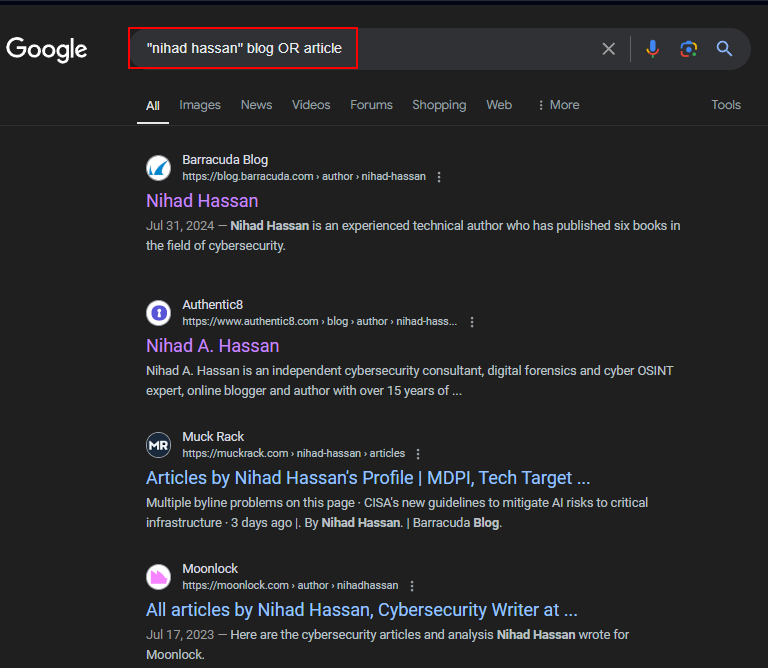
Figure 8 - Search for articles and blogs written by a specific name using Google dorks
Investigating bio, contact, and relationship details
A Facebook user bio contains important information for OSINT gatherers. Aside from their names, education and the company they work for, a Facebook user bio may include a user's contact information, such as phone numbers and email addresses, in addition to links to other social media profiles, blogs or personal websites.
For each piece of information in a user bio, we should execute specific OSINT searches.
Investigating contact information (phone numbers and emails)
This includes searching for target phone numbers and email addresses.
Reverse phone lookup services
There are many online services that allow us to find the caller's name by reverse-searching their phone number. Here are some online services:
- Truecaller: Phone number lookup
- Ipqualityscore: Free reverse phone number lookup
- NumLookup: Reverse phone lookup
- Spydialer: Free reverse phone number lookup
- Lookify: Another reverse phone number lookup
WhatsApp/Telegram/Signal presence
Some online services allow us to receive user ID or their name from popular internet chat messaging applications, such as Telegram and WhatsApp, by providing their phone numbers:
- Callmebot: Get Telegram ID from phone number
If we have the target username (for example, we can start by using the same Facebook username), we can use the Telegram global search function found in the top-right corner of the Telegram App (see Figure 9).

Figure 9 - Search for a Telegram username
To identify if the target Facebook user's phone number is registered on WhatsApp, try adding the number to your phone's contact list. WhatsApp uses the WhatsApp contact list and the native contact list stored on your mobile phone to identify registered WhatsApp users.
Public directories and databases
There are several public directories and databases where you can search for information associated with a phone number:
- Whitepages: Find people and contact info (email address, phone numbers, and mailing addresses)
- TruePeopleSearch: A free people search service with updated records on nearly every single adult living in the US
To find links to white pages websites worldwide, check WHITEPAGES.FR.
Email addresses
When having a target email address, we should utilize the following online services to find any information related to it:
Email verification tools
Verify if the email is correct and functioning:
- Hunter: Validate email addresses and identify related domain names
- EmailChecker: Email verifier and checker
- Verifalia: Free email address validator
Data breach databases
We should search within data breach repositories to see if the target Facebook email address appears in previously breached websites. These databases can reveal compromised credentials and associated accounts (such as accounts on other platforms with the same email address) and may display exposed personal information.
Here are some search engines for breached websites:
Domain registration records
If a Facebook user's bio includes one or more websites, we should investigate these domains. This investigation should include:
- WHOIS Lookup
- Domain History
- Associated IP Addresses
- Website Content Analysis
- Linked Websites
I have already created a dedicated guide on revealing website ownerships that describes all these techniques.
Examining posts, reactions, and engagement patterns
A Facebook post can provide valuable insights into an individual or group's activities, interests and connections. Here are the key elements of a Facebook post and how OSINT gatherers can exploit them.
Post content
The text in the post can reveal information about the user's opinions, experiences and behavioral patterns. The post may contain links to external resources, tags connecting to other Facebook users and multimedia content such as images, videos or shared articles. Location check-ins, attended events and timestamp data can also provide important contextual information about user activities and movements.
To search within a specific Facebook user profile, go to their profile page (I'm using Facebook on the web browser) and then click on the three dots in the right-hand corner of the profile page (see Figure 10).
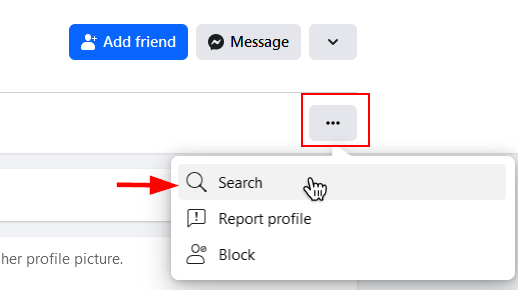
Figure 10 – Search within a specific Facebook user profile
Facebook posts may contain, in addition to text, an image (or many images) or a video. In that case, we can use a third-party service to download these media files onto our device to inspect them further using other tools.
- Fdown: Facebook video downloader
- Fdownloader: Download Facebook videos with high-quality
- Snapsave: A Facebook video downloader with low and high quality 1080p - 2K - 4K
When analyzing Facebook videos using sentiment analysis tools, we should extract text from them first. Here are some tools to facilitate this task:
- Piktochart Video: Convert video to text, support 60 languages. Requires registration with email to use the service
- Restream: Transcribe video to text using AI technology
- Maestro: Video to text
Every Facebook post displays the original publication date and time. The timestamp is displayed using the viewer's local timezone (see Figure 11).
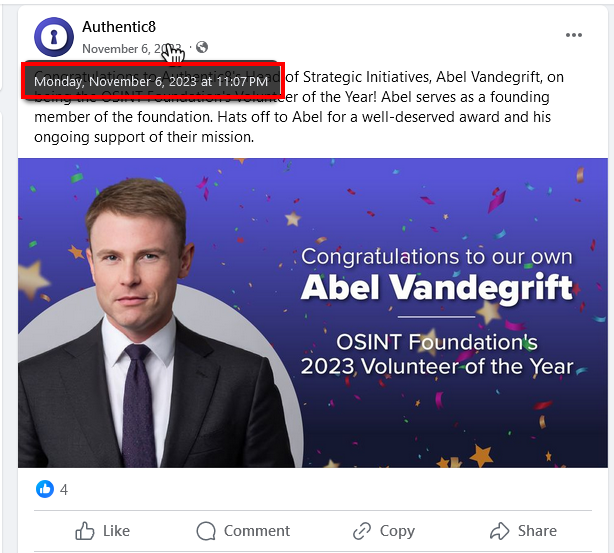
Figure 11 - Viewing Facebook post timestamp
When a post has been edited (new content added or deleted), Facebook displays a link "View edit history" in the post menu (see Figure 12). However, depending on user privacy settings, some edits may be hidden.
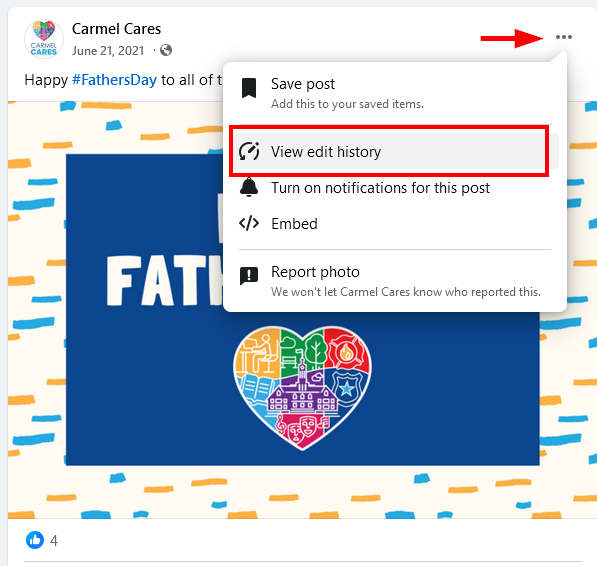
Figure 12 - View post-edit history
Using the Wayback Machine, we can check a public Facebook post edit history or previous versions.
We should take care of the following considerations regarding Facebook post timestamps:
- Post timestamps can be changed through page settings. We should consider this fact and cross-reference important posts' timestamps with other resources.
- Scheduled posts will display the publication time, not the scheduling time.
Post engagement
This includes reactions, comments and shares. Facebook users can react to a post using Like, Love, Haha, Wow, Sad or Angry emotions, which clearly indicates their emotional response to the content. For example, analyzing reaction patterns to specific types of content can reveal a user's ideological leanings, interests and potential affiliations.
Comments provide deeper insights into users' thoughts about the post's contents, including agreements, disagreements or other debates. Comment analysis can reveal:
- User close circles and relationships
- Linguistic patterns of users
- Active time and frequency of interactions
- Links to external content or references—some comments may contain links to external websites, an image or video
Shares indicate the post's reach and virality, displaying its popularity and identifying users who actively amplify specific messages or ideologies.
Sentiment analysis
Sentiment analysis of text in posts and comments can reveal the user's emotional state or attitude towards a particular topic. This can be achieved using natural language processing techniques. Here are some tools for executing sentiment analysis on social media posts:
- Free Sentiment Analyzer: Perform sentiment analysis on English text
- Social Media Sentiment Visualization: Execute sentiment analysis of text posts on different social media platforms such as Facebook, Reddit and Instagram
To recap, here is a quick guide of OSINT tools you can adopt as your own Facebook investigation techniques.
| OSINT Task | Tool / Service | Primary Function | Outcome / Insight |
| User ID & Profile Discovery | Lookup-ID.com | Find unique Facebook user IDs | Identify and cross-reference target profiles |
| Username Correlation | Whatsmyname.app | Reverse-search usernames across platforms | Reveal linked accounts and aliases |
| Image Verification | Tineye | Reverse image search | Locate reused or associated profile images |
| Metadata Extraction | ExifTool by Phil Harvey | Inspect EXIF data in images/videos | Analyze timestamps, geolocation, and device info |
| Facial / Emotional Analysis | FaceReader | Detect facial expressions and emotions | Gauge emotional state or context from profile images |
| Text Sentiment Analysis | Social Media Sentiment Visualization | Analyze post or comment tone | Assess sentiment trends across Facebook content |
| Email & Breach Analysis | Have I Been Pwned? | Check compromised email credentials | Identify linked accounts or data leaks |
| Reverse Phone Lookup | Truecaller | Identify phone number owners | Verify user identity or contact authenticity |
| Historical Data Review | Wayback Machine | View past Facebook posts or profiles | Retrieve deleted or edited content for timeline analysis |
| Secure Research Environment | Silo for Research | Isolated browser for OSINT work | Protects investigator identity and ensures compliance |
Conducting safe and anonymous Facebook OSINT
Facebook remains one of the richest sources of open-source intelligence, offering unparalleled insight into personal networks, behaviors, and affiliations. By applying structured Facebook OSINT techniques, from profile and post analysis to multimedia and metadata review, investigators can uncover valuable leads while maintaining accuracy and compliance.
Remember to stay secure and anonymous while you research. Protect your identity and the intent of your investigation with a purpose-built digital investigations platform like Silo.
Facebook OSINT FAQs
What is Facebook open-source intelligence (OSINT)?
Facebook OSINT involves using open-source intelligence techniques to collect publicly available data from Facebook profiles, pages, and groups for investigative or research purposes.
How do you perform OSINT on Facebook safely?
Use isolated browsers or secure research environments like Silo for Research to protect your identity and maintain data integrity during investigations.
Can Facebook OSINT reveal hidden information?
Profile connections, comments, and group interactions can expose valuable relational data, although privacy settings may limit access.
Is Facebook OSINT legal?
Facebook OSINT is legal when limited to publicly available information. Analysts must comply with privacy regulations and use secure, policy-compliant tools like Silo for Research to ensure ethical collection.
Why should you use Silo for Research for OSINT investigations?
Silo for Research isolates your investigation from attribution risk, ensuring anonymous, policy-compliant collection of social media intelligence.
Tags Anonymous research OSINT research Social media

